U2F security keys help to keep your online accounts secure even if your passwords are compromised.
Passwords alone aren’t enough to secure your online accounts. Too many passwords are easy for hackers to crack, and even if you use unique, strong passwords, they could still be stolen any day in a phishing attack or data breach.
That’s why you need two-factor authentication (2FA). With 2FA, you can protect access to your online accounts even if your passwords are cracked or leaked — like having a second lock after your password.
Safer than SMS and often faster and more convenient than using an authenticator app on your phone, U2F security keys are one of the most secure methods for 2FA.
Here’s how U2F security keys work and how they can help you stay secure.
What is U2F?
What is a FIDO U2F security key?
How to use a FIDO U2F security key
What are U2F security keys used for?
How do U2F security keys work?
Pros and cons of FIDO U2F security keys
FIDO U2F vs. FIDO2
Stay secure with U2F and Proton
What is U2F?
U2F (Universal 2nd Factor) is an open standard that allows you to use a physical security key for two-factor authentication (2FA), giving you an additional layer of security for your online accounts.
Once you set up 2FA with an online account, you must verify your identity twice when you log in:
Step 1: You enter your username and password.
Step 2: You typically do one of the following to confirm your identity again and access your account:
- Enter a one-time passcode generated by an authenticator app or delivered by SMS.
- Use biometric data, like touching a fingerprint reader or scanning your face.
- Plug in or tap a physical security key, also known as a hardware token or FIDO U2F security key.
What is a FIDO U2F security key?
A FIDO U2F security key is a physical device that allows you to log in to an account using 2FA. Available in all shapes and sizes, most U2F keys are similar to USB thumb drives or key fobs, like this YubiKey by Yubico:

FIDO stands for Fast Identity Online, a set of authentication protocols developed and maintained by the FIDO Alliance(new window).
A nonprofit group, the FIDO Alliance comprises government agencies and over 250 major companies, including Apple, Google, PayPal, and VISA. Apart from promoting U2F, the group aims to develop new authentication standards to “help reduce the world’s over-reliance on passwords”.

How to use a FIDO U2F security key
To use a U2F security key, you’ll need to:
- Buy a U2F key and register it with the website or app you want to use it with.
- After entering your username and password, you’ll be prompted to plug the key in and usually press or touch a button to log in. For example, you touch the “Y” on the YubiKey above.
You can also use U2F keys with mobile devices if your operating system supports it. For example, Apple introduced support for security keys with iOS 16.3, released in January 2023.
Plug in the key (if you have a compatible key) or tap the key on the phone (if the phone and key are NFC(new window)-enabled) to authenticate for 2FA.
What are U2F security keys used for?
U2F security keys are one of the most secure ways of implementing 2FA (or other multi-factor authentication). As anyone can fall victim to a phishing attack or data breach, you need 2FA to protect your accounts in case your passwords are ever lost or stolen.
You can use a U2F key to set up 2FA for many websites and online services, including Google, Apple, Microsoft, and Proton.
With most services that support U2F, you can set up a U2F security key and an authenticator app for 2FA. So if one fails, you have the other as a backup.
Learn how to set up U2F security keys with Proton
Besides consumer applications, U2F keys are often used in industries requiring high-security standards and compliance, such as finance, healthcare, and government sectors.
Some businesses require employees to use a U2F key to access internal networks or a VPN(new window) while working remotely. In 2018, Google said it had eliminated successful phishing attacks(new window) on its more than 85,000 employees by requiring them to use U2F security keys for their work-related accounts.
How do U2F security keys work?
U2F keys use public-key cryptography(new window) to verify your identity. This works by generating a mathematically related key pair:
- A private key, which is kept secret on your U2F key
- A public key, which the online service (website or app) stores on its servers
A new key pair is created when you set up your U2F key for 2FA with an online service. The private key is retained on your U2F key, while the matching public key is registered with the online service.
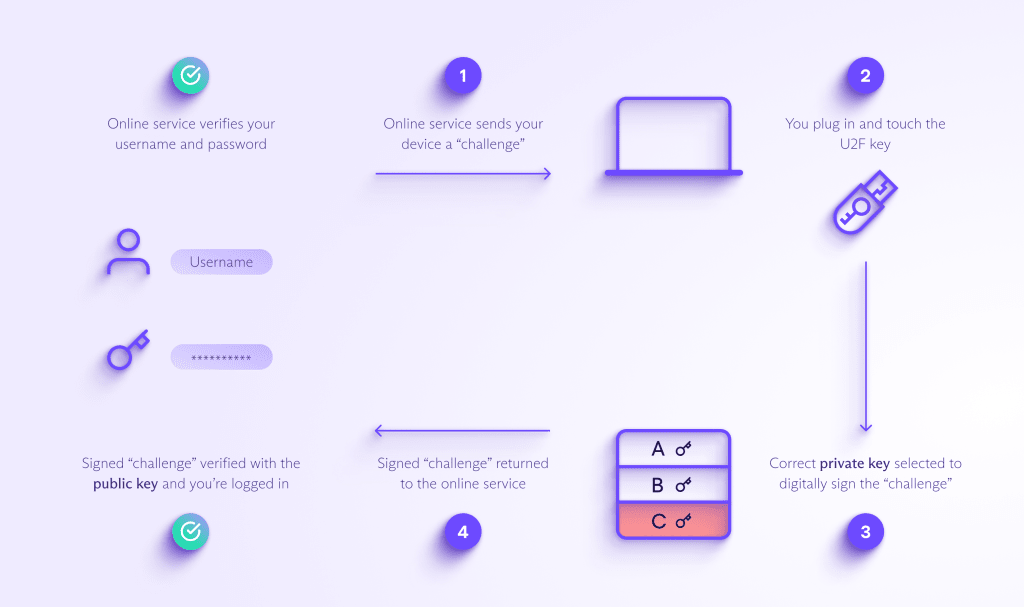
In simplified terms, here’s how you log in using a U2F key for 2FA:
1. Once you’ve correctly entered your username and password, the online service sends your computer, tablet, or phone a “challenge”, asking you to authenticate with a U2F key.
2. You plug the U2F key into a USB port on your computer and typically touch a button on the key (or plug it into your phone or connect with NFC).
3. From the private keys stored on your U2F key, your device selects the one that matches the online service’s public key and uses it to digitally sign the challenge.
4. Your device sends the signed challenge back to the online service, which verifies it with the stored public key and logs you in.
Pros and cons of FIDO U2F security keys
While U2F keys are considered one of the most secure methods for 2FA, they do have some downsides. Here are the main pros and cons.
Pros
Strong security
Both U2F keys and authenticator apps are much safer than SMS for 2FA because SMS texts are unencrypted and can be easily intercepted.
But U2F keys are considered even more secure than authenticator apps because:
- With U2F, only you have the private key stored on your U2F key. With authenticator apps, you have a “shared secret” (plaintext or QR code) shared between your device and the server.
- U2F keys digitally sign the 2FA challenge and transmit the response directly to the online service (see how U2F works above). In contrast, authenticator apps rely on one-time passcodes, which can be intercepted by eavesdropping or hacking (man-in-the-middle attacks(new window)).
However, no authentication method is 100% secure, and even U2F keys can be hacked(new window).
Ease of use
Once set up, U2F keys are quick and easy to use. You don’t need to open apps or manually enter one-time passwords. Just plug in the key and touch it (or tap it on your phone to connect with NFC).
You can use one key for as many services as you like as long as they support U2F.
Cons
No backup
With authenticator apps, you can copy the QR code or backup codes in case you ever lose access to your phone. Since you can’t duplicate the private keys stored on U2F keys, we recommend registering a second key with each online service as a backup.
Cost
While most authenticator apps are free to download, U2F keys cost money. Starting at around $20, U2F keys with the latest features can cost considerably more. And you may want to buy an extra key as a backup.
Risk of loss
Like other valuables, you must keep U2F keys safe. You can fit most on a physical keyring. But “nano” U2F keys are designed to remain in the USB port for convenience, so your accounts will be vulnerable if your device is lost or stolen.
What’s the difference between FIDO U2F and FIDO2?
Developed by the FIDO Alliance, FIDO2 is the latest authentication standard that’s set to supersede FIDO U2F. The main objective of FIDO2 is to introduce passwordless authentication(new window).
With FIDO2, instead of using a password and 2FA, you can log in to an account with just a FIDO2 security key or biometric data, like a fingerprint or face scan. For example, Apple uses the FIDO2 standard for its passkeys(new window), using Face ID or Touch ID.
As FIDO2 is backward compatible with FIDO U2F, it��’s fast becoming the new standard for 2FA and passwordless authentication. For instance, you can use FIDO2-enabled security keys to log in to Google or Proton using a password and 2FA.
Stay secure with U2F and Proton
To sum up, U2F security keys are one of the safest ways of using 2FA to beat phishing and keep your online accounts secure.
While any 2FA method is far better than using a password alone, choose U2F security keys or an authenticator app for 2FA rather than SMS, which is inherently insecure.
Many platforms, like Proton, allow you to set up two U2F security keys for your account or a security key and an authenticator app, so you always have a backup.
With Proton, you’ll see the following options after entering your Proton password:
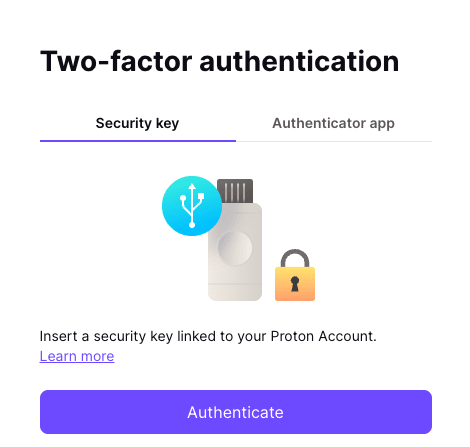
Simply plug in your U2F key, touch it, and you’re logged in.
If you haven’t already secured your personal information with a Proton Account, you can sign up for free. With end-to-end encrypted Proton Mail, Proton Calendar, Proton Drive, and Proton VPN(new window), no one but you can access your data. Not even Proton.
So join us, and stay secure with U2F and Proton!







